You are here
When cyber-attacks target hardware
The notion of cyber-attack usually brings to mind a virus meandering through lines of code. The assumption that these threats essentially involve software programs attacking other software programs is nevertheless reductive. Software functions thanks to a series of electronic components known as hardware. This includes the chip in a motion sensor that automatically turn on lights, as well as the dozens of cutting-edge processors found in a supercomputer.
Why (and how to) target hardware?
There are two typical scenarios. Side-channel attacks are a way of circumventing a software program's cryptographic security protocols , which are based on mathematical problems considered too complex to be resolved by those who do not have the key. Instead of cracking them, the attacker analyses how the hardware functions from its power consumption or its computation time during the execution of these algorithms, in an effort to break their secrets.
The other major category includes differential fault analysis, which induces faults within the hardware in order to block the computer system, for instance by making it heat up beyond its limits. In both cases, the purpose is generally to retrieve information rather than to destroy a device.
“These attacks were initially designed to steal the banking data on our chip cards,” points out Lilian Bossuet, a professor at Université Jean Monnet Saint-Étienne (southeastern France), and a member of the Hubert Curien laboratory.1 “These approaches are currently being applied to mobile phones, whose circuits are poorly protected. The situation is even worse for the Internet of things, where devices are omnipresent and barely secured, if at all.” Whether they target hardware or software, cyber-attacks exploit weaknesses, which cybersecurity researchers are seeking to correct before they are discovered by ill-intentioned individuals.
However, while a few lines of code can sometimes be enough to resolve a software's flaws, changing hardware is far more difficult. This is yet another reason to attack it, for while software is updated regularly, a computer's components may remain unchanged for many years, and replacing them each time there is a new threat would generate massive costs.
The Internet of things as a way in
“In general, there are two types of hardware attacks,” explains Clémentine Maurice, a CNRS researcher at the CRIStAL laboratory.2 “Some are carried out by hardware on hardware, and others on hardware by software. It is the latter, in addition to side-channel attacks, that I am particularly interested in.”
Attacks also take advantage of the fact that electronic devices are increasingly connected. While efforts have been made to protect computers, this is not necessarily the case for the other appliances connected to them. The presence of communicating objects with antennas is an additional weakness, as some attacks could be conducted from a few dozen metres away. “Systems are more and more complex and connected, and have to contend with increasingly twisted attack paths,” adds Bossuet. “The point of entry into a system, which is generally the least secured part, is not necessarily the ultimate target of an attack.” By way of example the researcher cites Stuxnet, a virus probably designed by US and Israeli services, which made its way into the Iranian nuclear programme in 2010.
Making hardware talk and ultimately break
Attacks on hardware by software often occur via the web browser, which executes a script in a programming language such as JavaScript. There is no need to download or install a dubious program, as such an attack can simply take place by clicking on a malicious website. “In hardware on hardware side-channel attacks, power consumption and electromagnetic fields provide clues regarding the hardware's activity,” says Maurice. “One can identify when it is carrying out cryptography activities, and strike at the right time in order to retrieve encryption keys.”
In particular, there is a fault attack called Rowhammer.js that gains access to a computer's entire physical memory by provoking electric charge transfers. The Rowhammer.js principle is frequently compared to hammering on a door that is of no interest until the vibrations resonate and open the entrance that is actually being targeted. While it is easy to imagine information technology as being entirely virtual and dematerialised, it is nevertheless based on electronic components that function using entirely concrete physical phenomena. “Electricity consumption and photonic emissions provide information regarding transistor activity,” states Bossuet. “We know that they consume the most power when they change state, in other words when they are processing information. Sometimes it is even possible to directly read the succession of 1s and 0s on an oscilloscope.” And if that is not enough, various artificial intelligence techniques can decipher this information with even greater precision.
Identifying users thanks to their chips
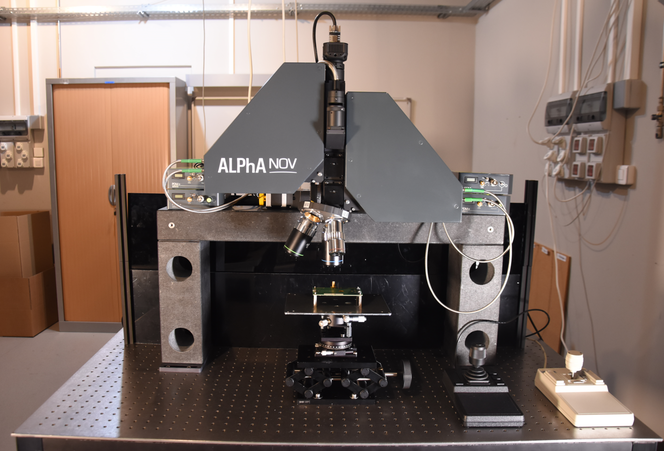
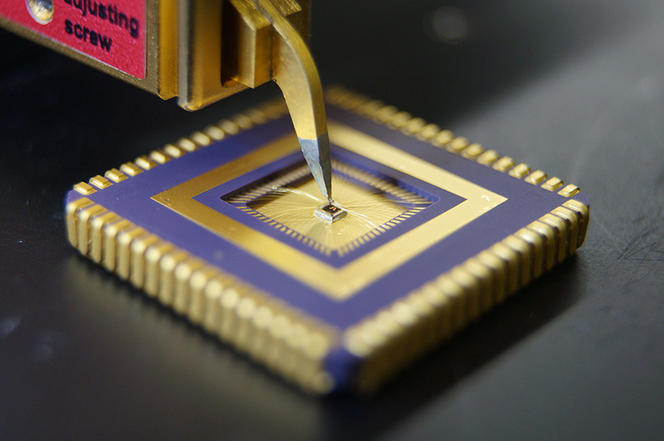
To explore these physical vulnerabilities even further, Bossuet's Sesam team targeted components using a four-laser platform created by the Alphanov company, of which the CNRS is a founding member. Researchers successfully modified bits of information during the execution of a program, changing instructions and values. Systems are then extremely exposed. Hardware has other shortcomings, and is especially targeted for fingerprinting. This concept involves identifying Internet users, often without their knowledge. It is not necessarily a matter of revealing their identity, but of recognising those who return to a website, seeing their activity before they visit, etc. The most well-known digital fingerprints are cookies, which often use IP addresses. While these elements are related to software, hackers and researchers realised that the same could be done with hardware.
Maurice’s Spirals team has developed, with Ben-Gurion University of the Negev (Israel), a fingerprinting technique named DrawnApart, which is based on a graphics processing unit (GPU). “We can distinguish between two GPUs of the same brand and model using the same operating system,” indicates Maurice. “With software fingerprinting, we start from scratch each time the user updates their browser. But here we can track them as long as they keep the same GPU, which probably will not be changed for a number of years.” How long the traces are kept is a key parameter, as there is little interest in following a user's navigation for a brief period of time.
DrawnApart functions by using JavaScript code executed by an Internet browser. The program forces the GPU to simulate drawing points in space in three dimensions. By compiling sufficiently precise statistics for this task, DrawnApart can identify tiny details specific to each chip. Although this technique can be thwarted by blocking Java or WebGL scripts, this deprives the user of legitimate functionalities that are based on these two technologies. For example, the content of numerous web pages will appear disorganised, and some media such as videos cannot be played.
Researchers from the Hubert Curien laboratory have also taken an interest in device fingerprinting. “We are studying physical unclonable functions, microelectronic ‘fingerprints’ that use tiny differences between transistors in normally identical circuits,” details Bossuet. “By measuring these differences, we can track the hardware, but also target a particular circuit during an attack.” This approach was initially developed to fight counterfeiting and theft of integrated circuits. Cybersecurity nevertheless prevailed, especially in detecting when a circuit is performing cryptographic computations, thereby revealing when to attack them.
How can such threats be fended off? “In trying to illustrate our work, we realised that security solutions are fairly similar to barrier gestures,” observes Bossuet. “For reasons of performance, numerous processors have cache memory zones, where they can store information that subsequently becomes vulnerable. We must think up new architectures that physically isolate critical information. However, enhancing security necessarily has a cost. While it is accepted for banking or military applications, it will be more difficult to bear for conventional or domestic uses.”
Explore more
Author
A graduate from the School of Journalism in Lille, Martin Koppe has worked for a number of publications including Dossiers d’archéologie, Science et Vie Junior and La Recherche, as well the website Maxisciences.com. He also holds degrees in art history, archaeometry, and epistemology.