You are here
Biometrics: Identification in Action

Fingertip, iris, face: to provide secure access to computers and online services, various parts of the body can be scanned in order to authenticate the user. But in fact, our hands can reveal much more than just our fingerprints. For example, a few letters entered quickly on a keyboard could be enough for the machine to identify who typed them. After several decades of progress in biometrical authentication techniques, researchers are now focusing on man-machine interactions, making use of the fact that each person has their way of handling a smartphone or computer, starting with how they type characters on a keyboard.
A strikingly clear identity
A new biometric authentication method through keyboard use appeared in France in 2007, driven by the work of Christophe Rosenberger and his team at the GREYC.1 The analysis of keystroke dynamics is based on a simple phenomenon: we all have our own identifiable way of using a computer or smartphone keyboard. Whether in light, rapid movements or slow, heavy strokes, the dynamics of our gestures easily reveals our identity. “To identify a person through their typing style, we only measure three parameters: the press and release times for each key, plus the time lapse between two keystrokes,” Rosenberger, a professor at ENSICAEN engineering school in Caen (northwestern France), explains. One need only enter a password five times for the software to “learn” that distinctive biometric keyboard signature, using a mathematical model. “For authentication, the machine compares the keystroke style of the password against the previously recorded model for that user.”
Futuristic though it may seem , identifying people by their typing is nothing new. Back in the days of the telegraph, operators with particularly sharp ears could single out certain users from the rhythms and tempos of their Morse code. This technique was used by the Russians and British during World War II to unmask Germans posing as allied soldiers on the clandestine radio networks.
Simplified passwords
Modern keystroke analysis works equally well with a conventional or touchscreen keyboard, or even a word entered directly on a webpage, acting as an extra security measure in combination with a password. It yields false positives in only 6% of the cases, “but this supposes that the person already knows the password,” Rosenberger emphasizes. This form of gesture recognition provides a low-cost security solution, because, unlike other biometric methods, it requires no separate peripheral device. “Not all computers have a fingerprint reader, but they all have a keyboard!” the researcher points out, underlining the simplicity of the technique: “Typing a password is an everyday, automatic action.”
Online banking is already taking a keen interest in keystroke dynamics. “At present, to access our accounts, we’re asked to enter elaborate, complex passwords that most people store somewhere on their computers, which is not very secure,” Rosenberger emphasizes. By integrating typing style into the security system, passwords could be simplified—to the relief of millions of computer users. No more 15-character passwords including punctuation marks, digits, special characters and upper-case letters. With keystroke analysis, we could soon be able to keep our favorite passwords, which could be birthdays, “12345” or the popular “qwerty” sequence.
At biometric rate
Just like keystroke dynamics, each authentication method, biometric or not, has its advantages and drawbacks. A combination of approaches therefore offers greater security. Google is leading the way towards a new era with its “Abacus” project, which aims to eliminate the need for passwords to unlock smartphones, and replace them with biometric authentication technologies that will identify the user’s face, voice or even breathing patterns. Another technique, developed by Christian Wolf and Natalia Neverova at the INSA (Lyon, France), in collaboration with Graham Taylor at the University of Guelph (Canada), consists in analyzing the way people interact with their phones. In fact, just like typing styles, each user has a unique way of handling a cellphone. “At first, we weren’t certain that the data would work,” reports Wolf, a lecturer and researcher at LIRIS.2 “But the results ultimately showed that movements are very clearly correlated to each individual.” This conclusion is backed by the findings of a preliminary study conducted by Google on 1,500 subjects.
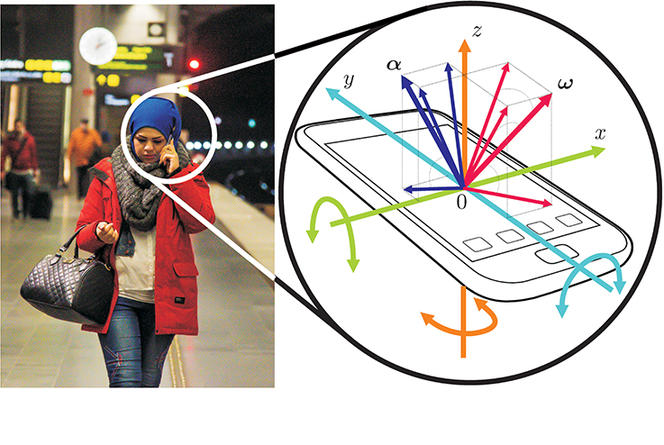
This form of gesture recognition relies on gyroscopic sensors and accelerometers integrated into each smartphone (see figure 1), which accurately measure the rotation and linear movement of the device. “We have developed a mathematical model whereby the machine learns to identify these movements and therefore the person that makes them,” Wolf explains. “Based on a technique called ‘deep learning,’ the method is refined automatically, drawing on a large body of user data compiled by Google. Like a child learning to distinguish the image of a cat, the device learns to recognize an individual through their movements.” One distinct advantage of the system is that it never transmits personal data, which remains entirely within the user’s control. The machine adapts to the user, and constantly integrates new data.
Can behavioral biometrics be “hacked”?
With gesture recognition, smartphone users do not need to enter a password: the device is unlocked automatically. “If after 30 seconds, it detects that someone else is using it—either through gestures or facial recognition, say—, it locks automatically,” Wolf points out. It is one way to make everyday life more convenient. And the reliability of this so-called “multimodal” project is nearly too high to be true. Combining these various identification techniques is more efficient than fingerprints or a PIN number.
As with a conventional password system though, there is the issue of fraud. Is it possible to imitate someone else’s typing style or way of holding a mobile phone? Also, don’t these kinds of behavior evolve over the course of a lifetime? Both Rosenberger and Wolf acknowledge that security breeches are “possible,” but are confident that they can be prevented by further refinements and regular updates of the algorithms involved.
Behavioral biometrics also raises questions on the protection of privacy—all the more so as, like the controversial technique of graphology, keystroke analysis could be used in psychological profiling. “It’s not foolproof, but we have been able to determine the user's gender in nearly 80% of cases,” Rosenberger says. The researcher reports similar results for age. If these findings are confirmed, keystroke dynamics could be used to identify pedophiles in chatrooms for minors or false reviews on e-commerce websites. According to Rosenberger, such techniques are “totally deployable tomorrow.” For Wolf, , in terms of biometric identification, “the machine sometimes seems to exceed human capabilities.”
- 1. Groupe de recherche en informatique, image, automatique et instrumentation de Caen (CNRS / UNICAEN / ENSICAEN) – “Monétique & Biométrie” (Computerized Banking and Biometrics) team.
- 2. Laboratoire d'informatique en images et systèmes d'information (CNRS / INSA-Lyon / Université Lyon 1 / Université Lyon 2 / Ecole Centrale de Lyon).
Explore more
Author
Léa Galanopoulo has a biology degree and is currently studying scientific journalism at Paris-Diderot university.